
Hey there, hope you’re doing well 🙂
As developers, we are busy typing away lines of code every single day, talking to multiple applications and services, exchanging and processing data over the internet. But how does all this transfer of data occur? What is a Network actually? It almost seems magical to think about a message that we type on our devices (phone, laptop, etc) being received by another person living in a different part of the world.
Let’s delve into some practical concepts supported by real-life examples of how data moves through the internet.

I. What is a Network?
Let’ s take an example of two people, Akash and Bhavna, to represent our client and server.
Akash and Bhavna, residing in different regions, share a strong friendship. Akash, eager to extend an invitation to Bhavna for his upcoming birthday celebration, crafts a personalized invitation. Within the realm of networking, every device is furnished with a distinct IP address, serving as a digital identifier. This IP address enables devices to seamlessly communicate within the network. In this analogy, Akash and Bhavna symbolize individual devices interconnected within the network fabric. Now, let’s delve deeper into the essence of IP addresses.

IP Address
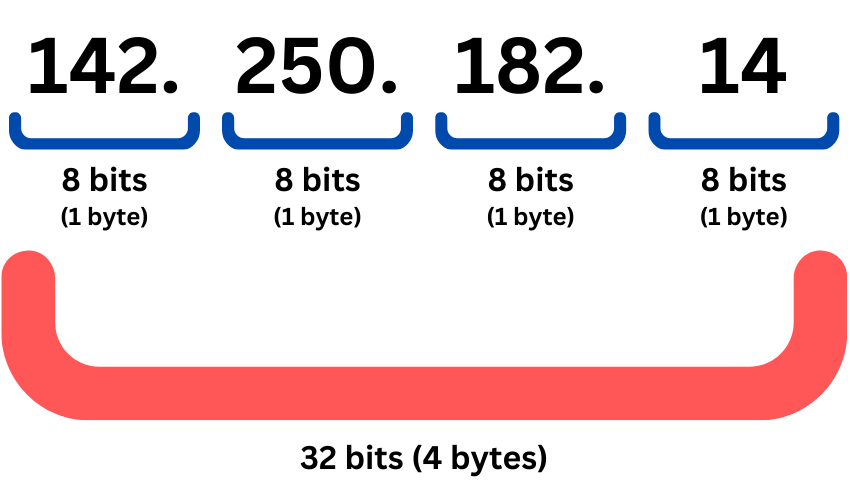
An IP address acts as a unique numeric identifier for every device connected to a computer network. There are two primary types of IP addresses: IPv4, which uses 32 bits, and IPv6, which uses 128 bits. Theoretically, IPv4 allows for approximately 4.3 billion distinct IP addresses.
To understand how this number is reached, consider that each bit in the 32-bit sequence can be either 0 or 1. With 32 positions, multiplying 2 by itself 32 times results in around 4.3 billion possible combinations.
However, due to various factors, such as design limitations and the internet’s rapid expansion, the actual number of usable addresses is significantly lower. This scarcity issue prompted the development and adoption of IPv6, which offers a vastly larger address space to accommodate the growing number of devices online.
IPv4 addresses are expressed in four octets, each containing 8 bits or a byte, with a range from 0.0.0.0 to 255.255.255.255. In contrast, IPv6 addresses consist of 8 groups of 4 hexadecimal digits, separated by colons, allowing for virtually infinitely unique IP addresses.
Despite the potential of IP addressing, the practical aspect of transmitting data from one device to another requires adherence to specific rules or protocols. Among these, the Internet Protocol (IP) governs the transmission of data over the internet.
In our analogy, Bhavna’s mailing address serves as her IP address, while Akash’s invitation represents a data packet transmitted over the internet. This analogy helps illustrate the fundamental role of IP addresses in facilitating communication between devices on a network.
II. Sending data over a network
Continuing with our example of Akash and Bhavna, let’s explore how data transfer in computer networks mirrors their invitation exchange. Picture Akash preparing an envelope for the invitation. On this envelope, he meticulously notes down both his and Bhavna’s details. Here, Bhavna’s information on the envelope corresponds to the IP and TCP headers, while the actual invitation inside the envelope resembles the payload or data of the packets.
IP (Internet Protocol) and data packets
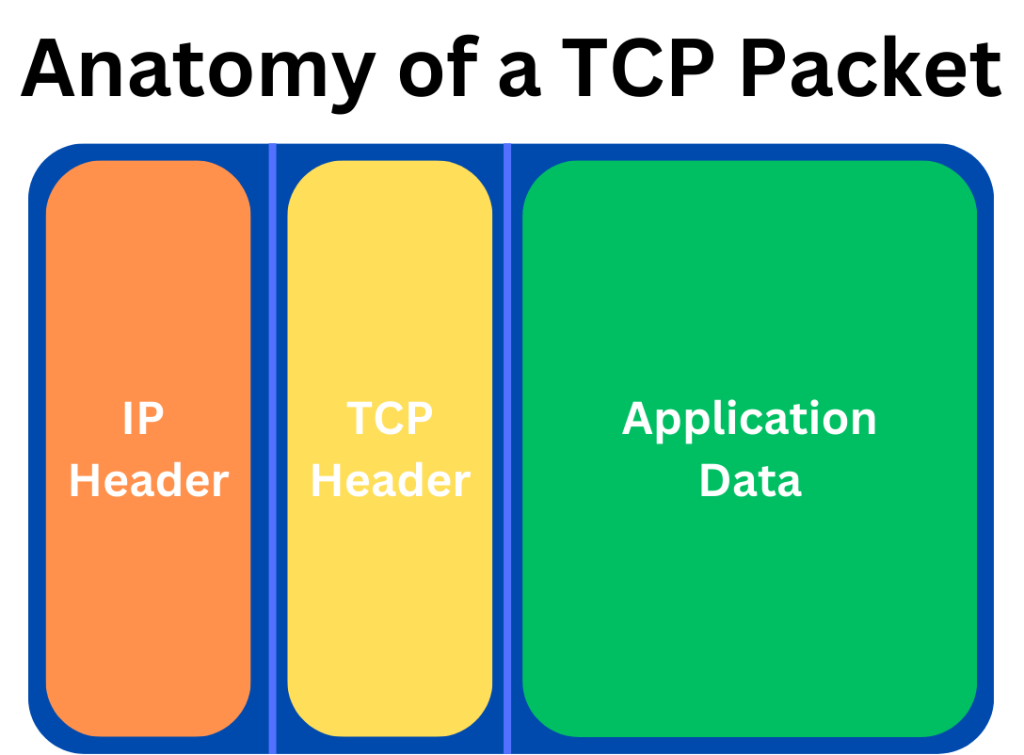
Just like Akash sends an invitation in an envelope, data is transferred over a network in the form of data packets. These packets consist of a header, data (payload), and a trailer or footer. The header contains important information, such as the source and destination IP addresses, which are crucial for our understanding as developers.
The header is specifically referred to as the IP Header. Usually, data is divided into multiple packets, and they may not arrive in the exact order they were sent. Transmission of data can occur in two ways :
- Connection oriented transmission – TCP
- Connectionless oriented transmission – UDP
TCP (Transmission Control Protocol)
When transmitting a large amount of data, we often split it into multiple packets. TCP ensures the accurate transmission of these packets, ensuring they arrive in the correct order. To illustrate, imagine Akash sending a multi-page letter to Bhavna. He numbers each page to ensure Bhavna reads them in the correct sequence. Similarly, TCP assigns a sequence number to each packet, allowing them to be reassembled accurately at their destination.
By combining TCP and IP, we not only ensure precise data delivery to the intended recipient but also facilitate packet reassembly upon reaching their destination.
This leads to further questions: How are connections established between devices? What happens if data is lost or not sent during transmission? Let’s delve deeper into the inner workings of TCP to explore these aspects.
3-way handshake
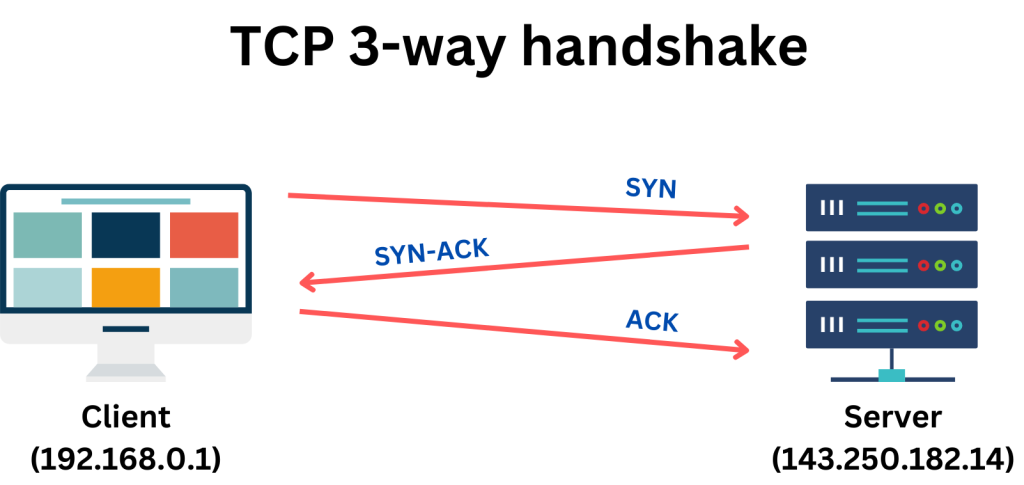
As mentioned earlier, data transmission involves dividing it into packets, which can be susceptible to loss. TCP addresses this by establishing a reliable connection through a process known as the 3-way handshake. Here’s how it works:
Step 1: The client sends a connection request to the server, including a sequence number and a Synchronisation (SYN) flag, to initiate a new connection.
Step 2: Upon receiving the request, the server responds with its own SYN flag, an Acknowledgement (ACK) flag, and a new sequence number calculated from the client’s sequence number. It also includes an acknowledgment number, indicating the previous sequence number plus one.
Step 3: Upon receiving the server’s response, the client sends back an ACK flag with an acknowledgment number, similarly incremented from the previous sequence number.
Once this handshake is completed, bidirectional communication can commence. If a data packet is sent but doesn’t receive acknowledgment, TCP assumes it was lost and triggers a retransmission, ensuring reliability. However, TCP’s reliability comes at the cost of increased overhead and slower transmission speeds due to its meticulous delivery mechanism.
UDP (User Datagram Protocol)
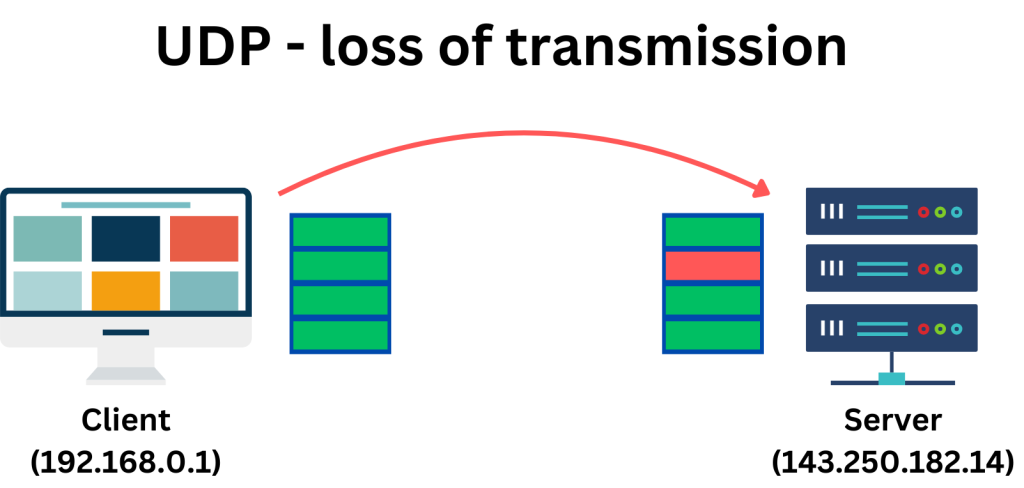
Unlike TCP, which prioritizes reliable data transmission through acknowledgments and retransmissions, UDP emphasizes speed and efficiency.
While UDP sacrifices some reliability compared to TCP by not attempting to resend lost packets or reorder them, it offers faster data transmission. This makes UDP ideal for scenarios where speed is critical and occasional packet loss is acceptable.
UDP serves various purposes in the following scenarios:
- Online Gaming : In online gaming, responsiveness and low latency are crucial for a seamless
gaming experience. UDP’s fast transmission and lack of retransmissions make it suitable for gaming applications, where occasional packet loss is tolerable if it means reducing latency. - Video Streaming : Video streaming applications, such as live broadcasting or video conferencing, often prefer UDP over TCP. While TCP ensures accurate data delivery, UDP’s occasional dropped frames are acceptable to minimize buffering and maintain uninterrupted playback.
- VoIP (Voice over Internet Protocol) : VoIP applications like Skype, facilitating voice communication over the internet, benefit from UDP’s speed and efficiency. Real-time voice communication demands low latency and minimal delay, making UDP preferable for transmitting voice packets without the overhead of TCP’s reliability features.
In these scenarios, it’s often preferable to prioritize speed and efficiency over reliability by choosing UDP. This ensures smoother gameplay, uninterrupted streaming, and seamless voice communication.
Now that we’ve explored how data packets are transferred from one device to another and the intricate stages detailing the transport process, it’s evident that networking protocols like TCP and UDP play crucial roles in ensuring reliable and efficient communication over the internet. However, there’s another vital component that underpins the functioning of the internet, one that often goes unnoticed but is fundamental to our everyday online activities.
Enter DNS, the Domain Name System. Just as IP addresses serve as unique identifiers for devices on a network, domain names act as human-readable labels for websites and other online services. But how exactly do we translate these familiar domain names, like google.com or facebook.com, into the numerical IP addresses that computers understand?
DNS (Domain Name System)
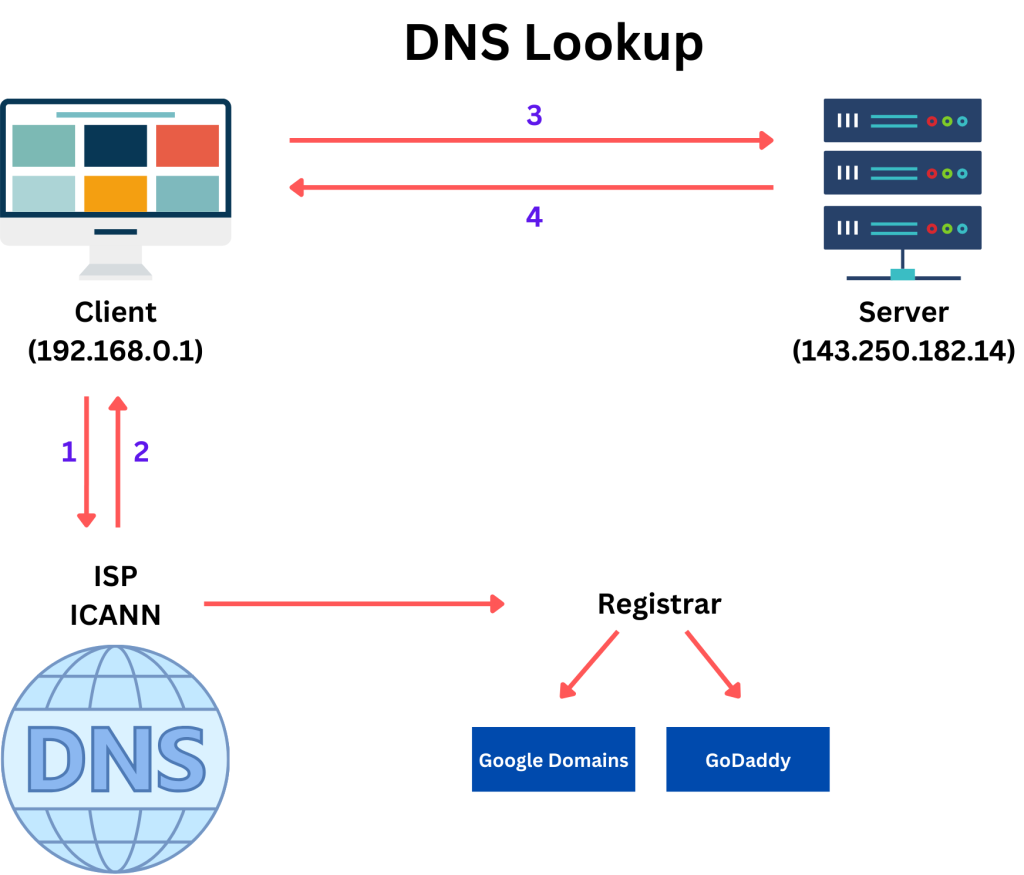
The Domain Name System (DNS) functions much like the internet’s phone book. Just as we maintain a contact list on our phones to avoid memorizing numerous phone numbers, DNS serves as a decentralized hierarchical naming system that converts user-friendly website names into numerical IP addresses.
When we enter a domain name like “google.com” into our web browser, the Domain Name System (DNS) translates it into an IP address (such as 142.251.211.238). This process enables our computer to identify where to send the request on the internet.
ICANN (Internet Corporation for Assigned Names and Numbers) oversees the overall coordination, security, and management of domain names within the DNS system.
ICANN and Domain Name Registrars
The fundamental question here is: who has the authority to assign domain names to specific IP addresses and, importantly, who has ownership over them? Take, for example, “google.com” – why can’t just anyone claim it? To address this, we need to grasp the roles of ICANN and Domain Name Registrars and how they differ.
Let’s draw an analogy: Imagine you’re opening a store in a shopping mall. ICANN acts as the management company overseeing the entire mall, while domain registrars function like individual lease providers for each store. Just as the mall management ensures the smooth operation of the entire mall, ICANN ensures the efficient functioning of the internet’s infrastructure.
When we want to register a domain name, we interact with a domain registrar, much like approaching a leasing company to rent a store space in a mall. These domain registrars are accredited by ICANN to provide domain name registration services. They assist us in finding available domain names and manage the registration process.
It’s essential to note that ICANN doesn’t directly own domain names. Instead, domain names are sold by authorized domain registrars, such as GoDaddy or Google Domains, which are approved by ICANN. These registrars maintain registration records and ensure that the domain is registered under our name.
DNS Records
In the Domain Name System (DNS), records store information related to domains or subdomains. Among these, the A (Address) record is the most common, linking a domain name to an IPv4 address. For example, if you request “google.com,” the DNS record would contain its corresponding IP address (e.g., 142.250.182.14), directing the request to the hosting server.
Imagine you send a request to “google.com,” connected to IP address 142.250.182.14. The DNS record for “google.com” holds this IP address. Upon receiving your request, the DNS server uses this record to route your request to the website’s server, which responds accordingly.
For faster future access, if a server has a static IP address (one that rarely changes), your computer can store it in its cache. This way, your computer retrieves the IP address from its cache instead of querying the DNS server when revisiting the same website.
To summarize, a server is a computer with a public IP address and domain name, configured with firewalls to handle public requests. When a client sends a request, the server processes it. DNS records and the DNS system are crucial for ensuring requests reach the correct server by mapping domain names to their respective IP addresses.
Conclusion
Understanding the fundamentals of networking is crucial for developers as it forms the backbone of modern computing. By grasping concepts like IP addresses, data packets, and protocols such as TCP/IP, developers can build more robust and efficient applications that leverage the power of the internet.
Let’s further explore the different layers of the network and the inner components of each of the layers in a future blog.
Till then, happy learning 🙂
